 Blog's Page
Blog's Page
In The Ever-evolving World Of Cybercrime, New Threats Often Emerge To Fill The Voids Left By Dismantled Botnets. Following The 2024 Disruption Of The Infamous IcedID And Qakbot, A New Apex Predator Has Claimed The Spotlight: Latrodectus.
Named After The Genus Of The Black Widow Spider, Latrodectus Has Spent 2025 Establishing Itself As The Go-to Delivery Mechanism For Ransomware Groups And Initial Access Brokers (IABs). This Blog Post Breaks Down The Technical Mechanics, The 2025 Distribution Trends, And How Your Organization Can Defend Against This Stealthy Threat.
Latrodectus Is A Sophisticated backdoor And Malware Loader Written In C. First Identified In Late 2023, It Rose To Prominence In Early 2025 As A Direct Successor To IcedID. Researchers Believe It Was Developed By The Same Creators—the Threat Group Known As LUNAR SPIDER.
Its Primary Objective Is Not Immediate Theft, But Rather persistence And Delivery. Once Latrodectus Infects A Host, It Acts As A "scout," Gathering System Information And Opening A Backdoor For More Destructive Payloads Like Lumma Stealer, Danabot, Or Even Full-scale Ransomware.
Modular Architecture: It Can Download And Execute Additional DLLs, EXEs, Or Shellcode.
Stealth-First Design: It Employs Heavy Obfuscation And Anti-analysis Checks To Bypass EDR (Endpoint Detection And Response) Systems.
Selective Targeting: It Specifically Checks For High-value Targets In The Financial, Automotive, And Healthcare Sectors.
In 2025, The Distribution Methods For Latrodectus Have Become Increasingly Creative. While Traditional Phishing Remains The Core, Threat Actors Like TA577 And TA578 Have Introduced New Wrinkles.
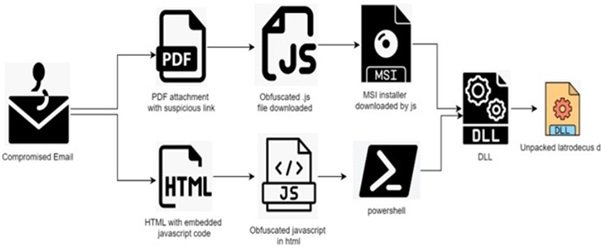
Most Infections Begin With A "thread-hijacking" Email. An Attacker Gains Access To A Legitimate Email Thread And Sends A Reply Containing A Malicious Link Or Attachment. Common 2025 Lures Include:
Legal Infringement Notices: Claims Of Copyright Violation.
Tax Documents: IRS Or W-2 Themed Lures (highly Active During Q1 2025).
DocuSign Impersonation: Fake "secure Documents" That Require The User To Download A File.
The Execution Process Is Designed To Baffle Automated Sandboxes:
The Redirect: The User Clicks A Link That Leads Through Multiple URL Shorteners (like cutt.ly) To A File Hosted On Legitimate Cloud Services Like Google Cloud Storage.
The Oversized JavaScript: A Massive, Obfuscated JavaScript File Is Downloaded. It Is Often Bloated With "junk Code" To Bypass Scanners That Skip Large Files.
The MSI Installer: The Script Triggers An MSI (Windows Installer) File, Which Sideloads A Malicious DLL—often Masquerading As A Legitimate Component From NVIDIA Or Microsoft.
Once The DLL Is Executed Via rundll32.exe, Latrodectus Establishes Contact With Its Command And Control (C2) Server. It Uses RC4 Encryption Over HTTP (typically On Port 8041) To Keep Its Traffic Hidden From Basic Network Monitoring Tools.
What Makes Latrodectus Particularly Dangerous Is Its Refusal To Execute If It Suspects It Is Being Watched.
Latrodectus Performs A "pulse Check" On The System. If It Detects It Is Running On Windows 10 Or 11, It Counts The Number Of Active Processes. If There Are Fewer Than 75 Active Processes, It Assumes It Is In A Virtualized Sandbox Environment And Terminates Immediately. For Older OS Versions, The Threshold Is 50 Processes.
The Malware Checks The Host's MAC Address. If The MAC Address Is Missing Or Belongs To A Known Virtualization Provider (like VMware Or VirtualBox), The Malware Will "self-destruct" To Avoid Being Analyzed By Researchers.
By Late 2025, Version 1.9 Of Latrodectus Was Observed Using AES-256 (CTR Mode) For String Decryption. This Represents A Significant Upgrade From The Simpler XOR Methods Used In Its Early Days, Making Static Analysis Nearly Impossible Without The Specific Hardcoded Keys.
A Major Development In Late 2025 Was The Discovery Of YiBackdoor. Cybersecurity Researchers At Zscaler And Red Canary Identified Significant Code Overlaps Between YiBackdoor, IcedID, And Latrodectus.
This Suggests That Despite International Law Enforcement Efforts Like Operation Endgame 2.0 (May 2025), The Developers Are Simply Rebranding And Refining Their Codebase. YiBackdoor Appears To Be A "lite" Version Of Latrodectus, Used For Rapid Testing Of New C2 Infrastructure Before The Main "Black Widow" Payload Is Deployed.
Defending Against A Loader As Sophisticated As Latrodectus Requires A Multi-layered Approach.
Monitor Process Count Anomalies: Look For Unusual Process Termination Patterns Where Common User Applications (like Chrome Or Outlook) Are Present, But The System Suddenly Stops Executing A New DLL.
Sysmon Logging: Monitor For Event ID 1 (Process Creation) Involving msiexec.exe Calling rundll32.exe From The %APPDATA% Or %TEMP% Directories.
Network Behavior: Block Or Alert On Outbound HTTP Traffic To Unfamiliar IPs On Non-standard Ports (specifically 8041 And 443 Without Valid SSL Certificates).
Disable Unnecessary Windows Script Host (WSH): Preventing .js Files From Running By Default Can Break The Infection Chain At The First Stage.
Strict MSI Policies: Implement "AppLocker" Or Windows Defender Application Control (WDAC) To Prevent Unauthorized MSI Installers From Running In User-writable Directories.
User Education: Conduct Simulations Specifically Focusing On email Thread Hijacking, As This Is The Primary Way Latrodectus Bypasses "gut Feeling" Security In Employees.
Latrodectus Is The Embodiment Of Modern Malware: It Is Patient, Intelligent, And Highly Adaptable. As We Close Out 2025, It Remains A Primary Entry Point For Some Of The World's Most Dangerous Ransomware Gangs. By Understanding Its "Spider-like" Behavior—hiding In The Shadows And Waiting For The Right Environment—security Teams Can Better Build The Webs Needed To Catch It.
As We Approach The End Of 2025, Latrodectus (also Known As "BlackWidow") Has Solidified Its Position As The Successor To IcedID And A Primary Gateway For Ransomware Deployments. While It Spent 2024 Rebuilding Infrastructure After Law Enforcement Disruptions, Its 2025 "waves" Have Been Characterized By Extreme Evasion And High-precision Targeting.
Ensuring Your Network Is Prepared Requires Moving Beyond Basic Antivirus. Here Is The 2025 Blueprint For Defending Against Latrodectus.
Latrodectus Rarely Acts Alone; It Is A Delivery Vehicle. In Late 2025, The Most Common Infection Chain Utilizes A "nested Deception" Model:
The Lure: Sophisticated email Thread Hijacking—where Attackers Reply To A Legitimate, Old Email Thread With A Malicious Link Or PDF.
The Redirect: Compromised Legitimate Domains (often googleapis.com) Hosting Oversized, Obfuscated JavaScript Files.
The Dropper: A Massive JavaScript File (bloated With Junk Code To Bypass Scanners) That Invokes msiexec.exe To Download A Remotely Hosted MSI Installer.
The Execution: The MSI Drops A 64-bit DLL Into %APPDATA%, Which Is Then Executed Via rundll32.exe.
Latrodectus Is Famous For Its "Pulse Check." If Your Security Sandbox Is Configured For Performance Rather Than Realism, The Malware Will Simply Remain Dormant.
The Threshold: On Windows 10/11, Latrodectus Checks The Total Number Of Running Processes.4 If There Are fewer Than 75 Processes, It Terminates Immediately.
The Hardware Check: It Validates The MAC Address And Checks For Virtual Machine (VM) Signatures.
Preparation Step: Ensure Your Sandboxing Environment Mimics A Real Workstation By Having Common Background Processes (browsers, Chat Apps, Update Services) Active.
In The Latter Half Of 2025, Latrodectus Has Moved Toward More "Living Off The Land" (LotL) Techniques To Hide Its C2 (Command And Control) Traffic.
C2 Traffic Monitoring: Latrodectus Typically Communicates Over port 8041 Using RC4-encrypted HTTP Traffic.6 Monitor For Outbound Connections On This Specific Port From Non-standard Processes.
Block URL Shorteners: Proactively Block Or Flag Clicks To cutt.ly, bit.ly, And t.co Within Corporate Emails, As These Are The Primary Bridges To The Final Payload.
Geo-Blocking & ASN Reputation: Recent 2025 Data Shows A High Concentration Of Latrodectus Infrastructure On Specific Autonomous System Numbers (ASNs) Associated With Budget VPS Providers In Eastern Europe And Southeast Asia.
If You Suspect A Latrodectus Infection, Your Team Should Hunt For These Specific Indicators Immediately:
| Indicator Category | What To Look For (2025 Specifics) |
| Process Names | rundll32.exe Or msiexec.exe Running From %APPDATA%\Roaming Or %TEMP%. |
| Persistence | Scheduled Tasks With Randomized Names Or "AutoRun" Keys In The Registry. |
| Mutex | Look For The Hardcoded Mutex String: runnung (the Developers' Common Typo). |
| API Hashing | Anomalous Usage Of RtlGetVersion And GetAdaptersInfo To Probe System Specs. |
As We Look Toward 2026, The Developers Behind Latrodectus Are Expected To Integrate AI-driven Code Mutation To Change Their File Hashes Every Hour.
Disable WSH: If Your Employees Don't Need To Run .js Files, Disable Windows Script Host Entirely. This Breaks The Infection Chain At The Dropper Stage.
Implement DLL Sideloading Protection: Use Tools Like Windows Defender Application Control (WDAC) To Prevent Unauthorized DLLs From Being Loaded By Legitimate Binaries Like rundll32.exe.
User Training: Traditional Phishing Training Is No Longer Enough. Employees Must Be Trained On thread Hijacking, Where The "sender" Appears To Be Someone They Were Talking To Just Yesterday.
Indicator Of Compromise:
URLs:
C2 Domain:
Hashes:
For More Detailed List Of IoC, Kindly Refer The Below URLs: